Note: Since Windows 8.1 was released on August 27, 2013, the Windows 8.1 Preview is no longer available for download.
Microsoft recently released the Windows 8.1 Preview, the future upgrade to Windows 8. Some of the changes are subtitle and are quite quickly overlooked; others are not. Changes included in Windows 8.1 are B.Y.O.D. (Bring Your Own Device), mobility, security, and user interface enhancements. With the promise of better user interaction on personal computers, Microsoft made some tweaks to Windows RT and Windows 8. Let's take a closer look into the user interface changes inside of Windows 8.1 Preview.
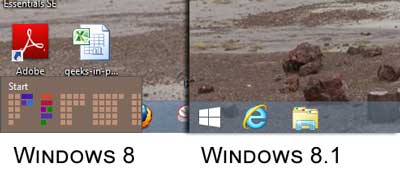
The Start button returns to Windows 8.1 Preview
The first thing you'll notice is that nothing appears to have changed. Right out-of-the-box, the only thing that caught my eye was the return of the Start button on the Desktop. You no longer have to hover your cursor in the lower left-hand corner of the screen. If you left-click on the Start button, it brings up the Start screen, not the Start menu from previous versions of Windows. If you right-click on it, the power user command menu appears without keyboard shortcuts. Pressing the Windows logo key  + X does the same thing but has the keyboard shortcuts (the underlined letter in the program's name). If you want a Start menu, you'll need a third-party app like Start8.
+ X does the same thing but has the keyboard shortcuts (the underlined letter in the program's name). If you want a Start menu, you'll need a third-party app like Start8.
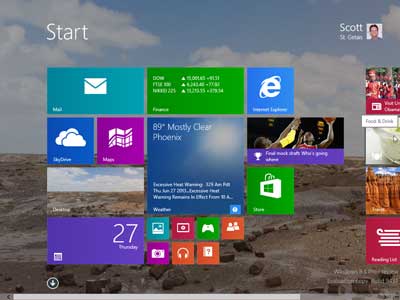
Smaller tile size on the Start screen inside of Windows 8.1 Preview
The Start screen has also undergone some changes. The tiles can now be resized smaller for non-touch devices like personal computers. You currently have four different tile sizes to choose from: large (8x8), wide (8x4), medium (4x4), and small (1x1). There is now a button at the bottom of the Start screen to toggle between it and the Apps screen. You no longer have to right-click the Start screen to bring up the Apps command bar. When you right-click on the Start screen, you get a customize button for adding names to groups of tiles. You no longer have to zoom out to do it. And now, if you zoom out, all you can do is select a group of tiles to zoom in on.
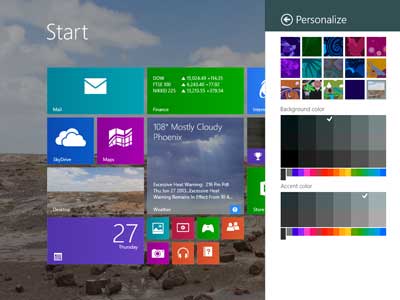
The Personalize options for the Start screen in Windows 8.1 Preview
The customization options for the Start screen have also been expanded. You can now use one of your images for the lock screen or play a slide show on it. You can now also change the accent color along with the background color. Not as many options as some third party programs like Decor8, but it's an improvement compared to Windows 8.
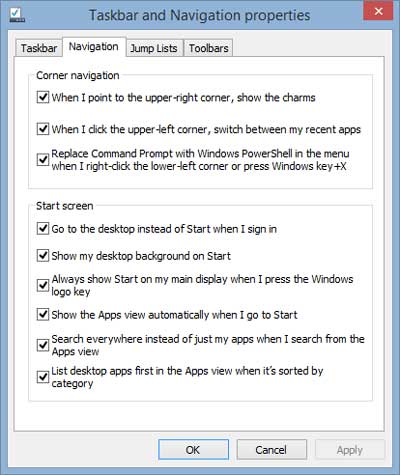
Taskbar and navigation properties inside of Windows 8.1 Preview
One of the most anticipated changes is the boot to Desktop option. It took a little hunting, but I did find it under Personalization > Taskbar and Navigation properties. It's there you can make Windows 8.1 go to the Desktop when you sign in. You can also have the Desktop background on the Start screen and set the Apps screen as the default when you left-click on the Start button.
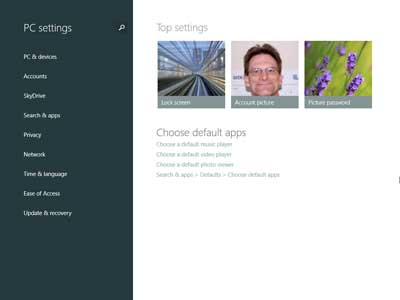
The redesigned PC settings inside of Windows 8.1 Preview
Another program that got a facelift was PC Settings. Microsoft redesigned it with expanded categories and sub-menus to include more settings. It's still not as complete as the Control Panel, but it's getting better. The new layout seems more proportionate on a computer screen, with the menu titles smaller. Overall, I would say the user interface inside of Windows 8.1 is an improvement over Windows 8. But without a Start menu, it will still be a hard sell to die-hard Windows users.
d009e90e-15ec-403a-b2bd-f0d591e06ebb|0|.0|96d5b379-7e1d-4dac-a6ba-1e50db561b04