Updated January 31, 2021. Microsoft's Enhanced Mitigation Experience Toolkit reached the end of its life on July 31, 2018, and is no longer available for download.
It seems like every day, a new software exploit or vulnerability is found. Software vendors work hard at keeping their software secure, but it can take time to test and deploy patches. So what can you do to protect your computer? The Enhanced Mitigation Experience Toolkit (EMET) from Microsoft does just that.
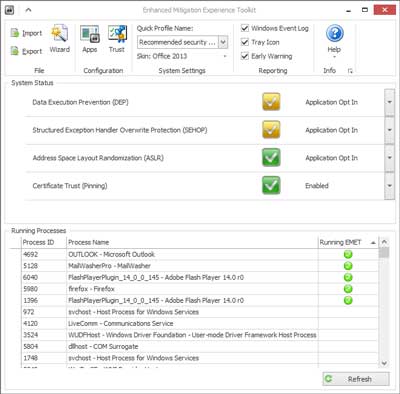
The main window inside of EMET 5
EMET is designed to prevent attackers from taking control of your system. It works as 'shim' in-between your programs and the operating system. EMET looks for the most common attack techniques and will block and terminate any program it is monitoring. EMET works alongside your favorite anti-virus and anti-malware programs for layered security.
I have been using EMET as part of my layered security for years and have written a few blogs on it. With each version, Microsoft keeps improving it. Some of the improvements in EMET 5 include Attack Surface Reduction (ASR), Export Address Table Filtering Plus (EAF+), and 64-bit ROP mitigations. Here's is the current list of mitigations EMET currently looks for.
- Structured Exception Handler Overwrite Protection (SEHOP)
- Data Execution Prevention (DEP)
- Heapspray allocation
- Null page allocation
- Mandatory Address Space Layout Randomization (ASLR)
- Export Address Table Access Filtering (EAF)
- Export Address Table Access Filtering Plus (EAF+)
- Bottom-up randomization
- Return Oriented Programming (ROP)
- Attack Surface Reduction (ASR)
There are two (2) different ways to configure EMET, a Graphic User Interface (GUI) and a command-line tool. It is best to configure EMET through the GUI since the command-line tool doesn't allow access to all EMET's features. The built-in configuration wizard will enable you to use either the recommenced settings, keep previous settings (upgrade install), or manually configure EMET (new install).
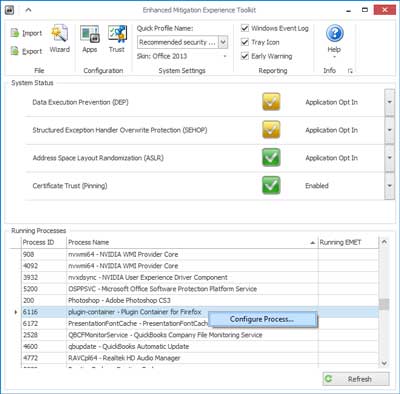
Easily configure programs to monitor in EMET 5
Once you have EMET installed, it's pretty easy to add programs to monitor. Just open the program you want EMET to watch and then open EMET. On the lower part of the main window, you will see Running Processes. Just find the program you want to monitor in the list, right-click on it, and select Configure Process. You will have to restart any program you have just configured inside of EMET.
de530379-e468-46de-9f96-d83d248b85c6|0|.0|96d5b379-7e1d-4dac-a6ba-1e50db561b04