Updated January 31, 2021. Microsoft's Enhanced Mitigation Experience Toolkit reached the end of its life on July 31, 2018, and is no longer available for download.
Keeping your computer secure has always been challenging. It seems like every week there is another exploit making the rounds. Nobody can predict what kind of attack hackers will use next. But you can protect your computer from the most common actions and techniques used with the Enhanced Mitigation Experience Toolkit 5.1 (EMET).
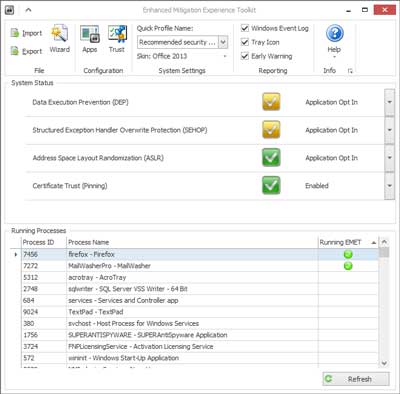
The main screen inside of EMET 5.1
What is EMET? It monitors selected programs (Internet Explorer, Microsoft Office programs, etc.) for known attack actions and techniques. When one of the several pseudo mitigation technologies is triggered, EMET can block or even terminate the program in question. It will also validate digitally signed SSL certificates inside of Internet Explorer. Here's is the current list of mitigations EMET currently looks for.
- Structured Exception Handler Overwrite Protection (SEHOP)
- Data Execution Prevention (DEP)
- Heapspray allocation
- Null page allocation
- Mandatory Address Space Layout Randomization (ASLR)
- Export Address Table Access Filtering (EAF)
- Export Address Table Access Filtering Plus (EAF+)
- Bottom-up randomization
- Return Oriented Programming (ROP)
- Attack Surface Reduction (ASR)
The about screen inside of EMET 5.1
EMET 5.1 includes the following improvements:
- Attack Surface Reduction (ASR) has been updated to limit the attack surface of applications and reduce attacks.
- Export Address Table Filtering Plus (EAF+) has been updated to improve and extend the current EAF mitigation.
- 64-bit ROP mitigations have been improved to anticipate future exploitation techniques.
- Several security, compatibility and performance improvements.
EMET can also be customized via the registry (see EMET manual for instructions). Here are a few of the items that can be modified:
- Enable unsafe configurations.
- Configuring custom message for user reporting.
- Configuring certificate trust feature for third party browsers.
- Configuring local telemetry for troubleshooting
- Configuring EMET Agent icon visibility.
Here's a quote from Microsoft's website:
The Enhanced Mitigation Experience Toolkit (EMET) helps raise the bar against attackers gaining access to computer systems. EMET anticipates the most common actions and techniques adversaries might use in compromising a computer, and helps protect by diverting, terminating, blocking, and invalidating those actions and techniques. EMET helps protect your computer systems even before new and undiscovered threats are formally addressed by security updates and antimalware software. EMET benefits enterprises and all computer users by helping to protect against security threats and breaches that can disrupt businesses and daily lives.
EMET should never monitor anti-malware and intrusion prevention or detection software, debuggers, software that handles digital rights management (DRM) technologies or software that uses anti-debugging, obfuscation, or hooking technologies.
eb4b248c-1446-47cb-ab7d-19cd9a09e51e|0|.0|96d5b379-7e1d-4dac-a6ba-1e50db561b04